PHACK CTF 2021 - RAID Dead Redemption - Write Up
This is the write-up of “RAID Dead Redemption” challenge. This was my favorite challenge of the PHACK CTF.
You work at the special brigade of the cyber defense service of the police station of Montargis.
The hard drives of a woman have been seized and have just been transmitted to you.
She is suspected of having downloaded numerous PNG and JPG files of which she did not have the
intellectual property. But it seems that she had time to delete some evidence before the intervention.
Do your best to extract as much as you can! The manual of a suspicious software running on the
computer has also been found and sent to you to guide you in your investigation.
So we have the manual in pdf of the software, and 3 files, DISK 1,2,3 and the DISK2 is completely empty, and the DISK3 contain the same size of the first.
After few searches and learning what is happening, we understand that the notion of RAID5 virtualization is implicated. It implicates distribution of storage in different disk.
The problem is that we don’t have the content of the DISK2. So we need to recover it.
After a few searches of RAID5 notion we read that RAID5 rest on XOR. This is what is used to recover a disk, when is corrupted or missing.
So, to recover DISK2 file, we have to XOR bytes per bytes, DISK1 and 3.
We going to use this script (https://github.com/ITAYC0HEN/XOR-Files/blob/master/xor.py)
So yes, we have now the DISK2.
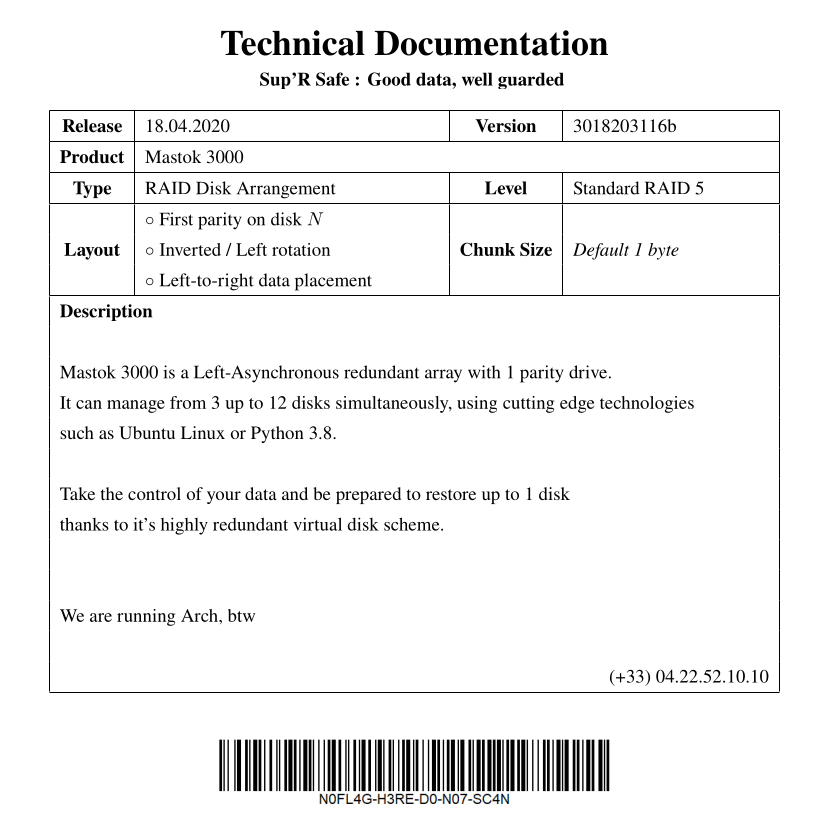
Now, we need to understand the notice, because this isn’t a normal RAID5 virtualization. We read that the first parity is on disk N, so It starts on the DISK3. Also, It includes left-Asynchronous redundant array, and classic left to right to read the data. This is represented with this schema :
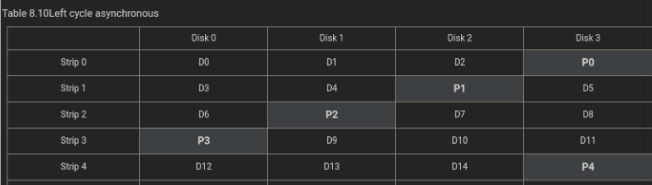
Here you can see where are parity bytes, they are here to recover a corrupted DISK with XOR like we said before. So, to recover the original data, we need to take every Data bytes(D1,D2,..), and not take the parity bytes taht you see here with the red points. Because this parity bytes, not contain the original data of the file that we want to recover.
So bytes of the diagonal top corner right / left bottom corner, should not be take to recover the original file.
I scripted a little python program to do this :
import sys
# Read two files as byte arrays
file1_b = bytearray(open(sys.argv[1], 'rb').read())
file2_b = bytearray(open(sys.argv[2], 'rb').read())
file3_b = bytearray(open(sys.argv[3], 'rb').read())
recover_byte_array = bytearray(len(file1_b))
compteur=0
i=0
j=0
while i < len(recover_byte_array)-1:
if compteur==0:
recover_byte_array[i]=file1_b[j]
recover_byte_array[i+1]=file2_b[j]
j+=1
compteur+=1
elif compteur==1:
recover_byte_array[i]=file1_b[j]
recover_byte_array[i+1]=file3_b[j]
j+=1
compteur+=1
elif compteur==2:
recover_byte_array[i]=file2_b[j]
recover_byte_array[i+1]=file3_b[j]
j+=1
compteur=0
i+=2
open(sys.argv[4], 'wb').write(recover_byte_array)
It takes 4 parameters, DISK1,2,3 and the file name of the file that we want to recover.
ANNNDD :

Here it is, we recover the file. Now, we need to find a flag.
We used Aperisolve and foremost to recover hidden files.
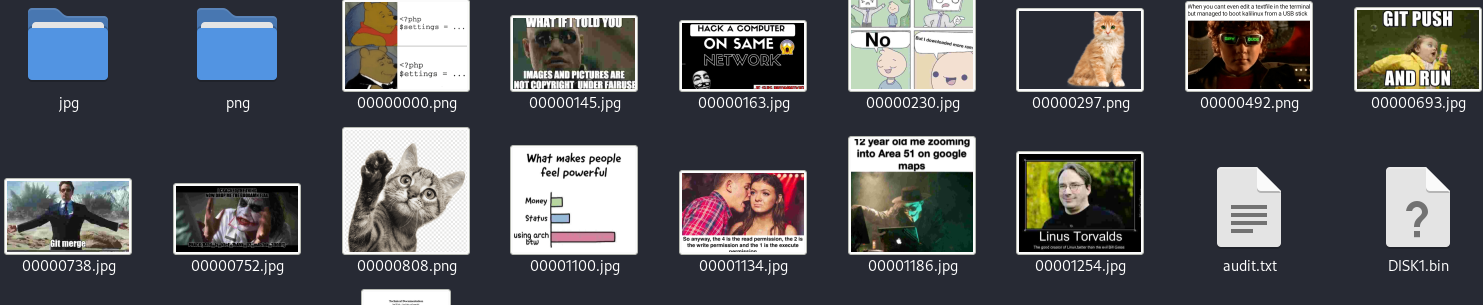
Many files right here..

PHACK{R41d_1s_N1cE_7hANk_U2_m4s7ok_3000!!}
Thanks to read this and thanks to the chall maker, this challenge was very cool.
Hope you enjoyed the write up.